No small business owner or principal needs to be told that cybersecurity is a constant risk. We hear about data breaches at large companies in the news on a regular basis these days. How can a business leader be sure they are compliant with CASL (Canadian Anti-Spam Legislation), GDPR (EU General Data Protection Regulation), the Digital Privacy Act (DPA), and PIPEDA (Personal Information Protection and Electronic Documents Act ) while at the same time ensuring their company is safe from cyber criminals who would like to take advantage of the smallest mistakes to steal the data you have?
We have previously published articles on GDPR and IT security emerging threats, which are still useful references. This article goes one step further and brings it all together along with newer regulations, and includes a quick checklist for businesses to review.
CASL vs GDPR
You may not think you need to worry about an EU regulation in Canada, but you'd be wrong! The EU's GDPR covers European residents regardless of their citizenship, which means that a Canadian person visiting Europe could theoretically be covered by GDPR. Also, a person who views your company's website from a European country could request to view the data you have collected on them.
Most Canadian companies will be familiar with CASL and may think that being compliant with CASL means that you are also in compliance with GDPR. This is also untrue. GDPR is much stricter than CASL in terms of protecting an individual's right to their data. There is a comparison chart below
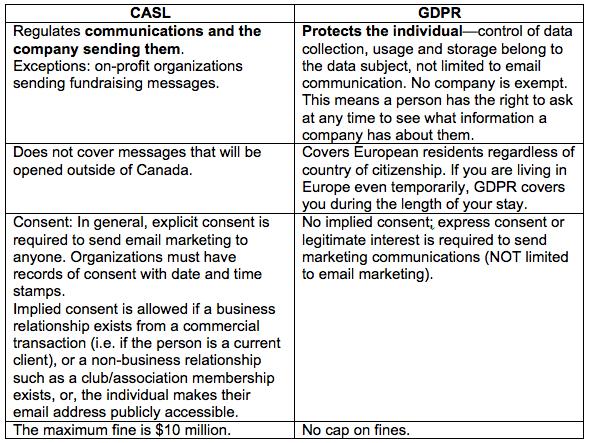
What is DPA and PIPEDA?
A recent amendment to the Digital Privacy Act (DPA) and the Personal Information Protection and Electronic Documents Act (PIPEDA) means that all Canadian organizations are required to report any data breach or cyber security incident which could potentially "lead to real risk of significant harm." Organizations must report the breach to both the federal government and the affected parties.
A checklist for businesses
Do
- Document consent: Be sure you have clear records of "opting in" consent for anyone you send marketing communications to.
- Have clear data policies in place: Your privacy, data collection and other cyber security policies should be clear to employees and clients/customers, stating what data you collect, how is it kept and how a person could access it if they wanted to.
- Be vigilant with regard to email attachments, links, and other phishing-type communications (including phone calls and text messages). Strange wording, slightly off punctuation and spacing, and strange email addresses are other signs to look for. Also train staff members regularly to be vigilant and to abide by all policies.
- Use strong passwords and require them of your staff and clients (for example, on client microsites or portals). In many systems you can set prompts to force regular password changes.
- Update your software when prompted (including on mobile devices)!
- Train your staff to be cybersecurity-aware. Be sure to train all incoming employees and include "reminder" training annually for all staff, including any recent updates or new threats to be aware of.
- In the event of a breach: Be sure to report the breach to those affected as well as the government, and follow your incident response plan.
Do Not
- Open email attachments or follow links in emails from people you don't know.
- Use the same password for multiple sites.
- Use public Wifi. Coffee shops, airports and hotels are not trusted sources for internet connectivity. If using Public WIFI, always use a VPN, or even better, use cell phone tethering.
- Use an unknown or unexpected USB key.
